While robust measures are available in businesses to protect their most sensitive data, there are still circumstances in which these data can be left exposed. This article explains how “confidential computing”, the trend in cybersecurity with great promise likely going to play a vital role in keeping our data private and safe.
With the acceleration of digitalization around the globe, businesses are struggling to keep pace with data privacy and security. In recent years, there were numerous cyberattacks and data breaches faced by industries and expected to rise exponentially. According to Cybersecurity Ventures, global cybercrime is to cost the world $10.5 Trillion by 2025, expected to increase by 15 percent per year over the next five years.
It is obvious that nobody wants their details or intimate photos to be stolen. And for businesses, the outcomes of data breaches can be even more worrying. Here comes “Confidential Computing”, one of the most promising advanced cloud computing technologies for a growing number of enterprises. Let’s see how and why this technology proves beneficial for the business in terms of cybersecurity.
Confidential Computing on the security block
With an expected compound annual growth rate of up to 95.6% by 2026. Confidential computing is poised to become one of the hottest trends in cybersecurity in the upcoming years. Especially in high-risk sectors such as finance and healthcare.
Confidential computing is a cloud computing technology that isolates sensitive information/data while processing. Further, keeps it in a secured enclave within the central base (CPU). The data and techniques used while processing is accessible only to the authorized user. It allows businesses to keep full control over their data even when it is running in a shared/public environment.
Every industry has sensitive data of employees, clients, or customers. With the security offered by confidential computing, they are free to move within the cloud. And can unlock various opportunities and services within their ecosystem. For example, banks usually face the threat of fraud and need a way to recognize and draw inferences about theft and fraudulent activities without revealing the private data of their customers.
Here Confidential computing with AI models helps to identify potential fraudsters while allowing the data to remain as such in the cloud that protects the data breaches or sharing data with other authorities.
How confidential computing could change the world?
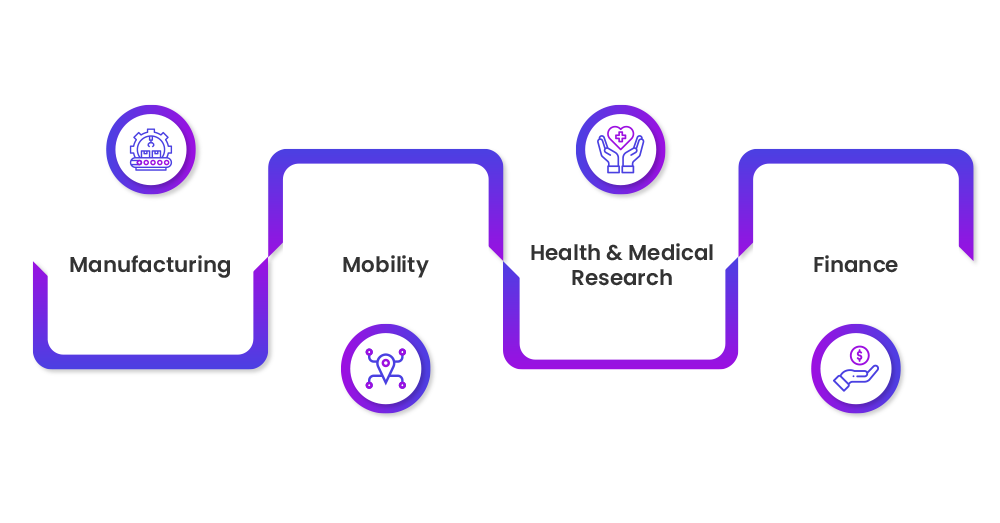
Insight the theory of this technology is of course a great start, but to deeply understand its potential, you should look at use cases. Confidential computing has itself the term “Confidential”, defining its use in cybersecurity. Since now every business relies on cybersecurity to look after its data at a certain level. However, this proves to be the most beneficial for those who usually face the highest risk while handling data such as Finance and healthcare.
- Manufacturing: As we all know that manufacturing industry consists of a lot of business data stored that abide them to share their data freely on the cloud. In such cases, this technology helps them to share and process their data without any insecurity in terms of safety concerns.
- Mobility: Confidential computing helps in the aggregation of sensor data from networked vehicles in an end-to-end encrypted way. This helps in the filtered output data that is beneficial for users, and partners, thus increasing customer experience.
- Health and Medical Research: Data of healthcare providers and patients is very crucial. Sharing information about medical research in the wrong hands, like about patient’s DNA or disease information could cause severe problems. In this context, Confidential computing helps in protecting these confidential data.
- Finance: Financial services are one of the most hacking targets that result in losses of hundreds of millions of dollars. This advanced cloud computing technology allows financial institutions to exchange data without leaving it at risk. Let’s say, if any bank shares data to carry out analysis, then it could make it easy to identify suspicious patterns.
Confidential Computing – A more confidential Future?
Consider the most personal information that is stored on your servers being operated by different companies around the world. Here it becomes necessary to protect these vital data from breach and hacking. Yes, data security has become an immense part of businesses. It is known that no system is 100% safe and likely never will be. But we are now entering a new era of global technology and advanced infrastructure that has practically unlimited potential to secure us and our data.
Data hackers continuously look for new vulnerabilities to exploit. And, when your network is not private but public, pivotal information about your organization can be at risk of being exposed. This information can be used against your authorities, partners, and even users.
We at Echelon Edge provide the solution of Network Security Management that helps in managing the policies to monitor access across the network of your organization.